Continuous visibility through sustained monitoring is a proven way to know threats and risks to your applications, data, and digital assets. Once they are identified, the next step is securing them from intelligent attacks, which is daunting. New malware strains and vulnerabilities are discovered daily, and even exploit kits are available on the darknet for purchase. Moreover, most of the attacks are AI-powered, and analyzing all possible vectors of attack is not easy. The attacker’s sophistication has grown with their confidence, although most of them are entrenched thousands of miles from the targets of their heists.
To sustain the cyber security edge and combat these prolific criminal minds, you need a solution that can be deployed in On-premise, Cloud, or Hybrid environments and collates, analyzes, and stores data using a secure connection. The solution must give you a comprehensive security view and should be quickly set up and scalable, with a lower cost of ownership and built-in resiliency.
This solution is IBM QRadar, which can simplify cyber security operations and streamline security costs as monthly operational expenses instead of significant capital investments.
IBM QRadar excels in every possible security task. It’s a SIEM solution that combines log, event, and flow data from millions of devices across On-premise, Cloud, and Virtual environments to correlate, analyze and differentiate real threats from false positives. The security intelligence platform uses security analytics and automation to accurately detect and prioritize threats and empower security analysts to mitigate any incident risks.
Key reasons to opt for IBM QRadar Cyber services with Aujas
IBM QRadar and Aujas Cyber Security Defense Center
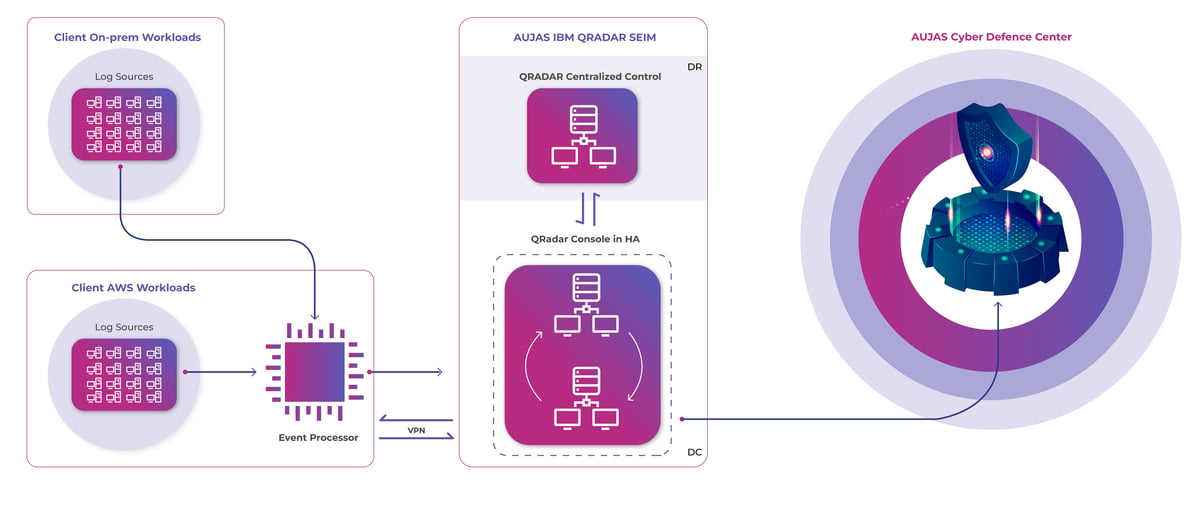
Initially, Aujas will deploy the IBM Event Processor on your premise to collect, store, parse and aggregate data from the integrated devices (log sources). The data stays within your technology environment, ensuring compliance. Aujas QRadar console works at high availability to avoid single point of failure and the console is directly accessible from Aujas Cyber Defence Centre for continuous monitoring. IPSec connectivity is established between the IBM QRadar console and Event Processor to enable Aujas CDC to monitor your network.
Aujas Cyber Defense Center – A snapshot
The CDC is powered by AI-ML to detect an attack in seconds and match its speed to prevent a breach. The source of the threat is quickly investigated, and a suitable response initiated to neutralize the attack.
Aujas CDC can evolve security defenses against web-based attacks, reduce ransomware occurrences, mitigate insider threats, ensure 24×7 monitoring, leverage analytics, enhance security governance, improve perimeter controls, and implement data loss prevention methods.
The CDC offers completely managed cybersecurity services based on the NIST cybersecurity framework to take on any complex attack. Aujas CDC offers highly advanced services such as Breach Automation, Cloud Security Services, Red Teaming, Access Governance, and 360 Degree Managed Detection and Response to transform cybersecurity posture. Aujas resource strengths include engineering teams, an elite group of threat hunters, product specialists, architects, and forensic experts who are always on the front-line to monitor and mitigate all known and unknown threats 24/7.
How the CDC can add value
- Proactive Threat Management: Ability to predict and neutralize threats
- Rapid Response: Quick to accurately identify an attack, provide notification and activate a response plan
- Contain Attacks: Validate, investigate, and raise alarms based on the severity of threats. Provide recommendations to minimize the impact of an attack and contain threats
- Automated AI-driven Breach Prevention: Automation to replace manual, mundane, and repetitive cyber defense processes
- ML-driven Incident Response: Incident analysis based on Machine Learning driven techniques for faster investigation
- SOAR: Employ Security Orchestration and Automation (SOAR) to improve incident response and standardization of processes
- Security Analytics: Application of security analytics across endpoints, users, networks, and applications to provide insights on attack
- Incident Remediation: Accelerated remediation for known and unknown threats
- Dark Web Monitoring: Provide visibility into the hacker community and underground marketplaces for any stolen data
Conclusion
The digitized world is highly connected, and it’s not advisable to remain agnostic in a dynamic threat landscape. You need an integrated cyber defense approach to secure your global infrastructure spread across geographies. Cyber attacks are not a possibility. They don’t get obsolete or irrelevant; instead, it is a dangerous certainty. Early action to build resilience can help you act more decisively to ensure these attacks are not compromising your connected infrastructure. By adopting the combined strength of Aujas CDC and IBM QRadar, you can future-proof your infrastructure by injecting resilience into your digital ecosystem so that it remains efficient, productive, and compliant.






